We Provide Reliable
IT Security
How We
Can Help
ITSG is an IT and Security solutions consulting firm and a value-added partner to leading security product manufacturers. Approaching security from a consultative perspective allows ITSG to combine the right blend of services and products to address our clients’ needs.
Leveraging ITSG will allow your organization to focus your resources back on your core business and ensure your IT systems are optimized to support you. ITSG is able to engage our clients at any of the 5 security phases below to help protect their digital assets.
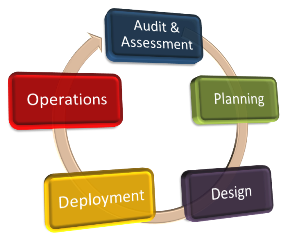
Audit & Assessment – we assist organizations in identifying risk within their environment
-
- Governance, Risk and Compliance
- Vulnerability Assessments
- Penetration Testing
Planning – working jointly with our client we develop a plan to address the areas of risk discovered during the Audit & Assessment Phase
-
- Security Polices and Procedures
- Security Polices and Procedures
Design – design the solution to meet the objectives of our client leveraging the polices and procedure identified in the Planning phase
-
- Architecture
- Implementation Plan
Solution Deployment – roll out of the components that best support the identified goal of the program
-
- Implementation
- Integration
- Training
Operations – on-going management services offering supplemental to completely outsourced support
-
- Management
- Monitoring
- Maintenance & Support
Our areas of expertise include:

Audit, Assessment & Compliance
- Gap Analysis
- Security Assessment Services
- Architecture Review
- Configuration Review
- Code Review
- Ethical Hacking Services
- Penetration Testing
- Web Application Testing
- Mobile Security
- Policy and Procedure Development
Cloud-Based Security
- Application Security
- Dynamic Application Security Testing (DAST)
- Static Application Security Testing (SAST)
- Anti-Virus
- Anti-SPAM
- Content Filtering
Infrastructure Security
- Routing (WAN)
- Switching (LAN)
- Wireless LAN (WLAN)
- WAN Optimization and Traffic Management
- PBX
- Firewalls
- Content protection
- Anti-virus
- Intrusion Prevention
- Application Intelligence
- SPAM
- Virtual Private Network (VPN)
- Host-Based Encryption
- Network Management
Are you Prepared For a Security Breach?
Schedule a Complementary Risk Analysis Today

